Halil Özkan
Keymate – Modern Authorization for Developers
#1about 2 minutes
The challenges of traditional in-code authorization logic
Hardcoded authorization checks quickly become unscalable and untestable, leading to a problem known as role explosion.
#2about 1 minute
Introducing Keymate for zero-rewrite authorization on Keycloak
Keymate extends Keycloak to provide fine-grained authorization without requiring application rewrites or data migration from existing identity providers.
#3about 1 minute
Externalizing authorization with service mesh and API gateways
Moving authorization logic out of the application code and into the infrastructure layer like a service mesh allows developers to focus on business logic.
#4about 1 minute
Using SDKs for optional fine-grained in-code control
For cases requiring more control, Keymate provides SDKs for Java, .NET, and JavaScript that support both REST and gRPC protocols.
#5about 1 minute
Leveraging an event-driven architecture for observability
Keymate is built on an event-driven model and uses OpenTelemetry to provide observability and enable parallel runs with existing systems for smooth migration.
Related jobs
Jobs that call for the skills explored in this talk.
Matching moments
02:43 MIN
An overview of Keycloak for identity management
Keycloak case study: Making users happy with service level indicators and observability
05:18 MIN
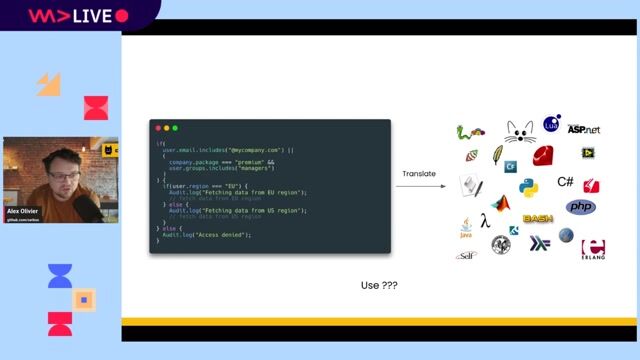
A modern approach using a decoupled authorization service
Un-complicate authorization maintenance
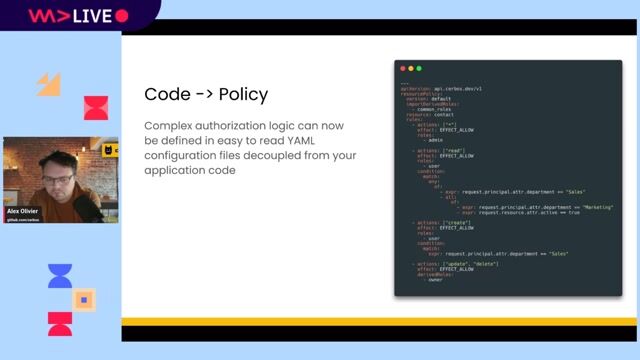
08:02 MIN
Implementing decoupled authorization with the sidecar pattern
Un-complicate authorization maintenance
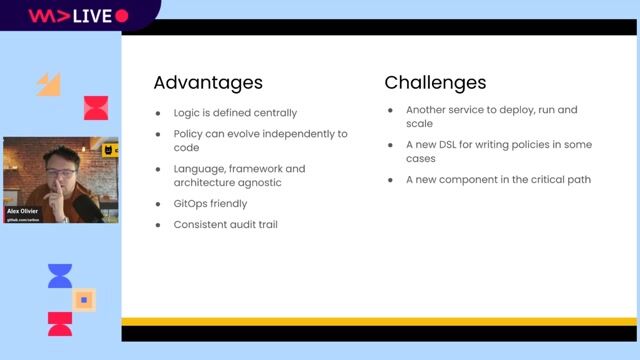
01:26 MIN
Using the open source project Cerbos for authorization
Un-complicate authorization maintenance
18:31 MIN
Implementing authentication with Keycloak, Quarkus, and JWT
Get started with securing your cloud-native Java microservices applications
02:10 MIN
Introducing the key players in an OIDC ecosystem
Delegating the chores of authenticating users to Keycloak
03:06 MIN
The challenges of embedding authorization in application code
Decoupled Authorization using Policy as Code
06:29 MIN
Introducing Policy as Code and Open Policy Agent
Decoupled Authorization using Policy as Code
Featured Partners
Related Videos
 23:42
23:42Delegating the chores of authenticating users to Keycloak
Alexander Schwartz
 1:00:00
1:00:00Un-complicate authorization maintenance
Alex Olivier
 27:15
27:15Keycloak case study: Making users happy with service level indicators and observability
Alexander Schwartz
 32:16
32:16Decoupled Authorization using Policy as Code
Anderson Dadario & Denys Vitali
 05:40
05:40Kalo: From Code Chaos to One-Click Polyglot Codegen
Brennan Nunamaker
 23:29
23:29Delay the AI Overlords: How OAuth and OpenFGA Can Keep Your AI Agents from Going Rogue
Deepu
 1:48:32
1:48:32Get started with securing your cloud-native Java microservices applications
Thomas Südbröcker
 26:55
26:55Navigating Application Modernization - Leveraging Gen-AI
Shaaf
Related Articles
View all articles


.gif?w=240&auto=compress,format)
From learning to earning
Jobs that call for the skills explored in this talk.








