Deepu
Delay the AI Overlords: How OAuth and OpenFGA Can Keep Your AI Agents from Going Rogue
#1about 4 minutes
Understanding the current state of AI security challenges
AI systems often have poor judgment, and the security domain is playing catch-up with the rapid evolution of AI agents and protocols.
#2about 3 minutes
Focusing on key OWASP Top 10 risks for developers
Application developers should focus on mitigating sensitive information disclosure and excessive agency, as these have a large attack surface under their control.
#3about 3 minutes
Why traditional RBAC fails for RAG systems
Traditional role-based access control (RBAC) is insufficient for RAG systems due to dynamic context and complex data relationships, necessitating a fine-grained authorization (FGA) approach.
#4about 5 minutes
Implementing OpenFGA to secure RAG data access
OpenFGA uses authorization models and relationship tuples to filter documents from a vector store, ensuring the LLM only receives data the user is permitted to see.
#5about 2 minutes
Mitigating excessive agency with zero trust tool access
Control an AI agent's tool access at the code level using zero trust principles, applying standard RBAC for simple cases and FGA for granular, user-dependent permissions.
#6about 1 minute
Securing third-party API calls using OAuth federation
Use OAuth 2.0 federation to allow AI agents to call third-party APIs on a user's behalf without handling raw credentials, using a broker to manage access tokens.
#7about 1 minute
Adding human guardrails with asynchronous authorization
Implement human-in-the-loop approvals for high-stakes actions by using the CIBA flow to send asynchronous authorization requests to users for confirmation.
#8about 5 minutes
Demoing step-up authorization and system architecture
A live demo showcases step-up authorization where an agent requests user consent before accessing sensitive data, followed by an overview of the application's architecture.
Related jobs
Jobs that call for the skills explored in this talk.
Matching moments

05:16 MIN
Addressing security risks and guardrails for agentic AI
Unlocking Value from Data: The Key to Smarter Business Decisions-

02:46 MIN
Overcoming legal and security roadblocks for AI adoption
The AI Skills Gap: What Tech Leaders Must Get Right
03:19 MIN
The overlooked security risks of AI and LLMs
WeAreDevelopers LIVE - Chrome for Sale? Comet - the upcoming perplexity browser Stealing and leaking

07:10 MIN
Managing the fear, accountability, and risks of AI
Collaborative Intelligence: The Human & AI Partnership

16:49 MIN
Q&A on AI adoption, tools, and challenges
Navigating the AI Wave in DevOps
01:40 MIN
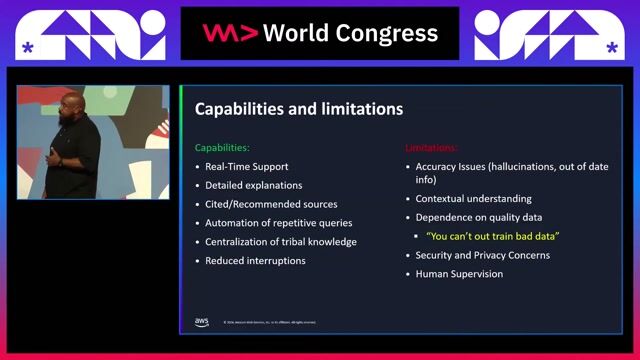
Addressing AI limitations with human oversight and security
Make it simple, using generative AI to accelerate learning

01:51 MIN
Final advice on security and responsible AI usage
WeAreDevelopers LIVE - Chrome for Sale? Comet - the upcoming perplexity browser Stealing and leaking

03:35 MIN
Understanding AI security risks for developers
The AI Security Survival Guide: Practical Advice for Stressed-Out Developers
Featured Partners
Related Videos
 29:00
29:00Beyond the Hype: Building Trustworthy and Reliable LLM Applications with Guardrails
Alex Soto
 30:36
30:36The AI Security Survival Guide: Practical Advice for Stressed-Out Developers
Mackenzie Jackson
 29:03
29:03On a Secret Mission: Developing AI Agents
Jörg Neumann
 26:47
26:47The State of GenAI & Machine Learning in 2025
Alejandro Saucedo
 28:27
28:27AI & Ethics
PJ Hagerty
 28:14
28:14Exploring 5 Key Applications of AI Abundance with Blockchain Assurance
ED MARQUEZ
 24:12
24:12From A2A to MCP: How AI’s “Brains” are Connecting to “Arms and Legs”
Brad Axen
 26:54
26:54Make it simple, using generative AI to accelerate learning
Duan Lightfoot
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.





TRUSTEQ GmbH



