Thomas Südbröcker
Get started with securing your cloud-native Java microservices applications
#1about 5 minutes
Introduction to the cloud-native security workshop
An overview of the workshop's goals, the final application architecture, and the open source technologies used like Keycloak and Quarkus.
#2about 19 minutes
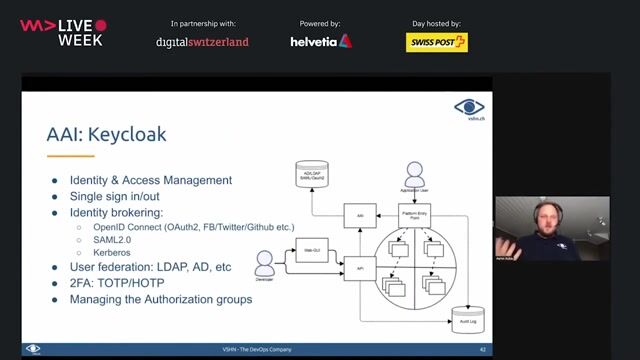
Implementing authentication with Keycloak, Quarkus, and JWT
A walkthrough of the authentication and authorization flow using Keycloak for identity management, Quarkus with MicroProfile for the backend, and JSON Web Tokens (JWT) for secure communication.
#3about 13 minutes
Securing the platform with an Istio service mesh
An explanation of Istio's core concepts, including the sidecar proxy model for traffic management, securing external access with TLS, and enabling internal security with mutual TLS (mTLS).
#4about 18 minutes
Setting up the IBM Cloud and Kubernetes cluster
A step-by-step guide to requesting a pre-configured Kubernetes cluster on IBM Cloud and accessing it using the integrated Cloud Shell.
#5about 21 minutes
Configuring the Istio ingress gateway with TLS
This lab demonstrates how to install Istio, expose its ingress gateway with a public DNS name, and secure it with a TLS certificate from Let's Encrypt.
#6about 6 minutes
Deploying and configuring Keycloak for identity management
Learn how to deploy Keycloak to Kubernetes and automate the creation of a security realm, users, and roles using a script and the Keycloak API.
#7about 7 minutes
Deploying the Java microservices to Kubernetes
This section covers deploying the web frontend, web API, and articles microservices to the cluster and configuring the Keycloak client with the correct redirect URI.
#8about 6 minutes
Enforcing strict mutual TLS for internal traffic
Discover how to apply an Istio policy to enforce strict mutual TLS (mTLS), preventing unauthorized internal services from directly accessing protected endpoints.
#9about 9 minutes
Implementing service-level authorization policies in Istio
Go beyond mTLS by creating Kubernetes ServiceAccounts and applying Istio AuthorizationPolicies to control which specific services are allowed to communicate with each other.
#10about 4 minutes
Visualizing traffic with Kiali and workshop summary
Use the Kiali dashboard to visualize the secured service mesh traffic and review the key application and platform security concepts covered in the workshop.
Related jobs
Jobs that call for the skills explored in this talk.
Matching moments

05:32 MIN
Understanding the core components of cloud security
Building Well-Architected applications

00:52 MIN
Summary and resources for getting started with Quarkus
Test-Driven Development: It's easier than you think!
05:27 MIN
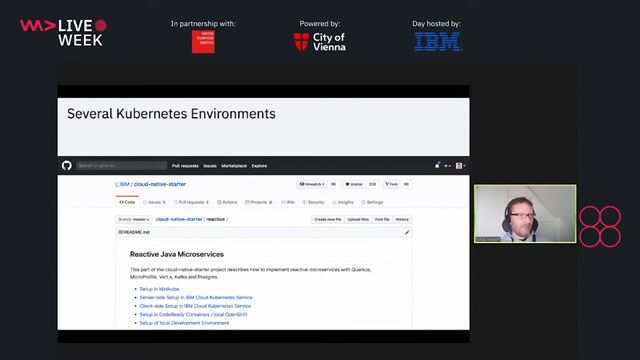
Deploying reactive apps and key takeaways
Development of reactive applications with Quarkus
02:52 MIN
Q&A on managed Kubernetes security in the cloud
Kubernetes Security - Challenge and Opportunity
11:25 MIN
Q&A on microservice architecture and security
Security Challenges of Breaking A Monolith
02:04 MIN
Centralizing security services in a Kubernetes ecosystem
DevSecOps: Security in DevOps

01:20 MIN
Building and securing the new microservices architecture
How to Destroy a Monolith?
03:26 MIN
Accelerating development with AI and security tools
30 powerful AWS hacks in just 30 minutes: Boost your developer productivity
Featured Partners
Related Videos
 37:55
37:552021: Familiar APIs on Kickass Runtimes #slideless
Adam Bien
 29:34
29:34You can’t hack what you can’t see
Reto Kaeser
 37:36
37:36Walking into the era of Supply Chain Risks
Vandana Verma
 27:15
27:15Keycloak case study: Making users happy with service level indicators and observability
Alexander Schwartz
 43:36
43:36Cloud-nativeApplications- What’s the buzz about
Jens Eickmeyer
 45:19
45:19Security Challenges of Breaking A Monolith
Reinhard Kugler
 28:21
28:21Developer Joy with Quarkus
Daniel Oh
 47:34
47:34Architecting API Security
Philippe De Ryck
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.

PROSOZ Herten GmbH
Herten, Germany
Junior
Intermediate
Senior
Java
Scrum
Kotlin
Microservices


Vesterling Consulting GmbH
€70-90K
Software Architecture


Akros Ag
Junior
Docker
Jenkins
Openshift
Kubernetes
Microservices
+1

Akros Ag
Junior
Docker
Jenkins
Openshift
Kubernetes
Microservices
+1

Akros Ag
Junior
Docker
Jenkins
Openshift
Kubernetes
Microservices
+1


Callista Group
Basel, Switzerland
Senior
Apache Kafka
Microservices