Reinhard Kugler
Security Challenges of Breaking A Monolith
#1about 7 minutes
Understanding the problems with a monolithic architecture
A monolithic video processing application faces challenges with scaling, high costs from idle power, and a lack of reliability.
#2about 2 minutes
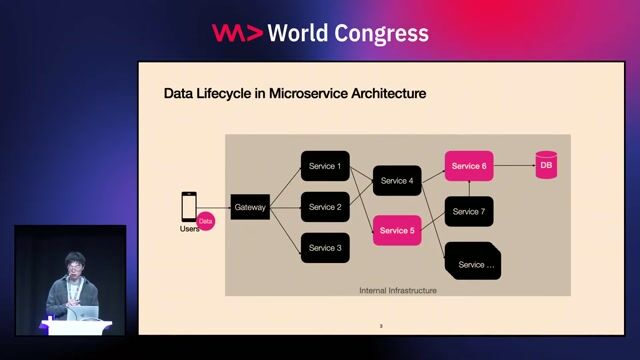
Decomposing the monolith into a microservice architecture
The application is broken down into distinct services like an API, a message broker, a transcoding worker, and S3 storage.
#3about 2 minutes
Securing container images and the software supply chain
The initial step of containerization reveals that official base images often contain known vulnerabilities, highlighting supply chain risks.
#4about 4 minutes
Defining trust boundaries for authentication and authorization
Breaking down the application creates new trust boundaries between frontend and backend components, requiring robust authentication and authorization.
#5about 8 minutes
Using bucket policies and pre-signed URLs for S3 access
AWS S3 access is controlled using bucket policies for broad rules and pre-signed URLs for providing temporary, specific access to objects.
#6about 3 minutes
Preventing malicious uploads with input validation
An AWS Lambda function can be triggered on file uploads to S3 to perform validation and prevent attackers from hosting malicious content.
#7about 5 minutes
Analyzing the impact of a container vulnerability
A vulnerability in a transcoding library like FFmpeg can be exploited through a malicious file, leading to code execution and access to secrets within the container.
#8about 2 minutes
Comparing security trade-offs of monoliths vs microservices
While microservices increase the attack surface and complexity, they offer better isolation, making privilege escalation more difficult than in a monolith.
#9about 11 minutes
Q&A on microservice architecture and security
The speaker answers audience questions about using AI in security, starting new projects, and identifying threats in a microservice architecture.
Related jobs
Jobs that call for the skills explored in this talk.
Matching moments

01:20 MIN
Building and securing the new microservices architecture
How to Destroy a Monolith?

03:07 MIN
Challenges of modernizing and scaling monolithic frontends
Web-Fragments: incremental micro-frontends migration approach for enterprise
01:29 MIN
The challenge of data security in microservice architectures
Safeguarding Sensitive Data Access At Scale with Privacy-Enhancing Technologies

13:10 MIN
Audience Q&A on practical micro-frontend challenges
Micro-frontends anti-patterns
04:21 MIN
Break down monolithic problems into microservices
End the Monolith! Lessons learned adopting Serverless
01:22 MIN
Leveraging containerization for improved security posture
Kubernetes Security - Challenge and Opportunity
02:34 MIN
The flawed debate between monoliths and microservices
Microservices? Monoliths? An Annoying Discussion!

05:12 MIN
Navigating security risks when creating developer content
WeAreDevelopers LIVE - Should We Respect LLMs? Is Rust Taking Over? Developers as Content Creators and more
Featured Partners
Related Videos
 29:34
29:34You can’t hack what you can’t see
Reto Kaeser
 33:20
33:20DevSecOps: Security in DevOps
Aarno Aukia
 50:06
50:06Single Server, Global Reach: Running a Worldwide Marketplace on Bare Metal in a Cloud-Dominated World
Jens Happe
 25:05
25:05Microservices? Monoliths? An Annoying Discussion!
Eberhard Wolff
 51:41
51:41Climate vs. Weather: How Do We Sustainably Make Software More Secure?
Panel Discussion
 44:30
44:30Securing Your Web Application Pipeline From Intruders
Milecia McGregor
 37:36
37:36Walking into the era of Supply Chain Risks
Vandana Verma
 47:34
47:34Architecting API Security
Philippe De Ryck
Related Articles
View all articles.gif?w=240&auto=compress,format)



From learning to earning
Jobs that call for the skills explored in this talk.

Peter Park System GmbH
München, Germany
Senior
Python
Docker
Node.js
JavaScript



Vesterling Consulting GmbH
€70-90K
Software Architecture





GULP Information Services GmbH
GIT
Next.js
TypeScript
AWS Lambda
Amazon DynamoDB
+1