Adam Larter
Break the Chain: Decentralized solutions for today’s Web2.0 privacy problems
#1about 2 minutes
The developer's responsibility as a custodian of user data
Centralized Web2.0 architectures create data honeypots that lead to frequent and costly breaches, highlighting the developer's role in protecting user information.
#2about 3 minutes
Rethinking data ownership beyond centralized systems and blockchain
Users should own their data, and while blockchain is a decentralized technology, it is not suitable for storing private, personally identifiable information.
#3about 2 minutes
Understanding the financial and compliance risks of data breaches
Data breaches result in significant financial costs, reputational damage, and steep fines under regulations like GDPR.
#4about 1 minute
Shifting from centralized databases to personal data stores
The proposed architectural shift moves user data from a central server to a personal data store where applications "log into the user" with consent.
#5about 4 minutes
Introducing Decentralized Identifiers and Verifiable Credentials
Decentralized Identifiers (DIDs) provide a unique identity, while Verifiable Credentials (VCs) are cryptographically secure, tamper-evident claims about that identity.
#6about 2 minutes
How to present and query verifiable data securely
Verifiable Presentations (VPs) are used to share selected data from VCs, and Presentation Exchange (PEX) provides a standard query language for requesting it.
#7about 5 minutes
Bridging Web2.0 and Web3 with OpenID Connect standards
OpenID Connect extensions for Verifiable Credential Issuance and Verifiable Presentations allow existing identity protocols to work with decentralized data.
#8about 6 minutes
An overview of the Affinity decentralized identity platform
The Affinity platform provides tools like the Affinity Vault for personal data storage, Affinity Login for authentication, and Affinity Elements as a control plane.
#9about 3 minutes
Announcing the Affinity IOTA framework for developers
The IOTA framework is an end-to-end orchestration layer that simplifies decentralized data access by moving queries to the user's front-end data store.
#10about 1 minute
Implementing the IOTA framework with a simple SDK
Developers can integrate decentralized data requests into their applications with just a few lines of code using the Affinity SDK.
#11about 1 minute
Building an Internet of Trust with a new architecture
The Affinity Trust Network provides the tools to build applications where the user controls the consent boundary, with future plans for open-sourcing components.
Related jobs
Jobs that call for the skills explored in this talk.
Matching moments
02:28 MIN
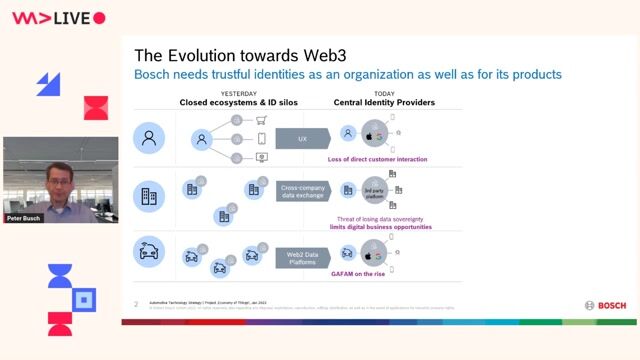
The problem of centralized platforms and data sovereignty
Trust as the Key Concept in Future Mobility

04:18 MIN
Solving for data sovereignty and identity control
Giving the individual control of their data: Open Source Decentralized Web Nodes
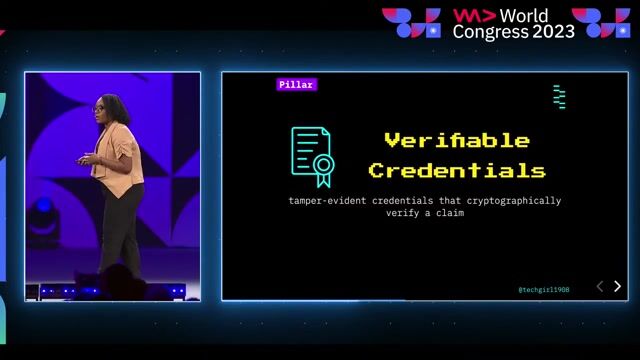
01:49 MIN
How verifiable credentials enable trustless interactions
Refactoring the Web
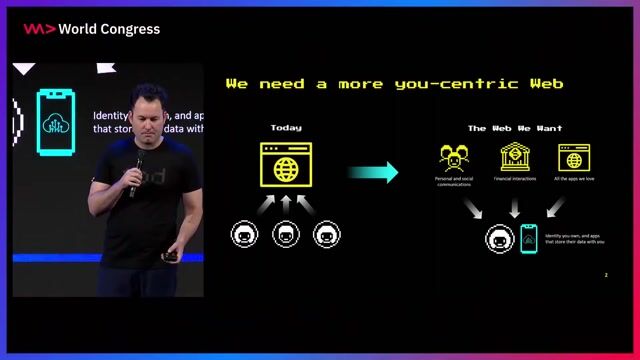
04:52 MIN
The vision for a user-centric web called Web5
Giving the individual control of their data: Open Source Decentralized Web Nodes
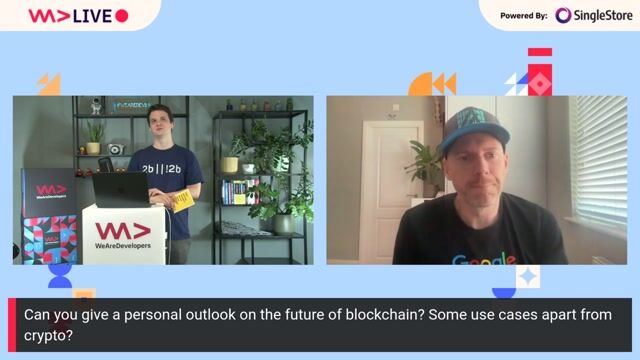
05:13 MIN
The future of blockchain, decentralization, and identity
Future-Proofing FinTech With Blockchain Technology

08:30 MIN
Answering questions on data, scalability, and accessibility
Web3: Embracing the Next Era of the Internet Within a Web2 Landscape

02:41 MIN
The vulnerability of centralized digital identity
Refactoring the Web
06:00 MIN
Q&A on data ownership, monetization, and competing tools
A Data Mesh needs Open Metadata
Featured Partners
Related Videos
 37:37
37:37Refactoring the Web
Angie Jones
 30:04
30:04Giving the individual control of their data: Open Source Decentralized Web Nodes
Angie Jones, Mike Brock, Daniel Buchner, Markus Sabadello & Nalin Mittal
 26:34
26:34Web3: Embracing the Next Era of the Internet Within a Web2 Landscape
Darrel Idiagbor
 28:50
28:50Demystifying Crypto & Web3: A Technical Journey Through 15 Years of Innovation
Ed Marquez
 56:45
56:45Trust as the Key Concept in Future Mobility
Peter Busch
 26:41
26:41Overcome your trust issues! In a world of fake data, Data Provenance FTW
Jon Geater
 30:32
30:32Debunking the Top 10 Myths about Web 3
Ed Marquez
 27:55
27:55Going Beyond Passwords: The Future of User Authentication
Gift Egwuenu
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.


iov42
Vienna, Austria
Senior
Java
Spring
Ethereum
PostgreSQL
Blockchain
+3

Stolzberger GmbH
Berlin, Germany
Remote
Ethereum
Blockchain
Microsoft Office
Continuous Integration






TRUSTEQ GmbH