Gift Egwuenu
Going Beyond Passwords: The Future of User Authentication
#1about 3 minutes
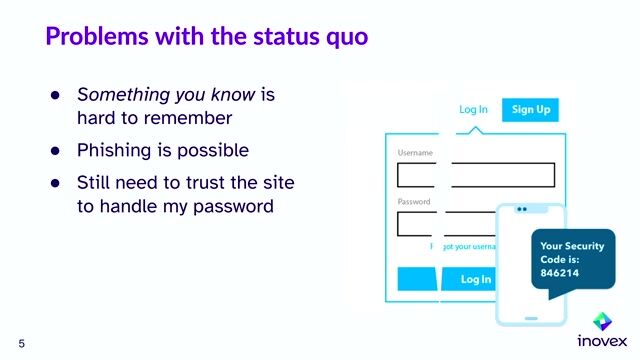
The inherent weaknesses and risks of traditional passwords
Traditional passwords are no longer secure due to common user mistakes, frequent data breaches, and sophisticated cyber attacks.
#2about 5 minutes
Best practices for creating and managing secure passwords
Following guidelines like using character combinations, avoiding personal information, and using password managers can significantly improve account security.
#3about 4 minutes
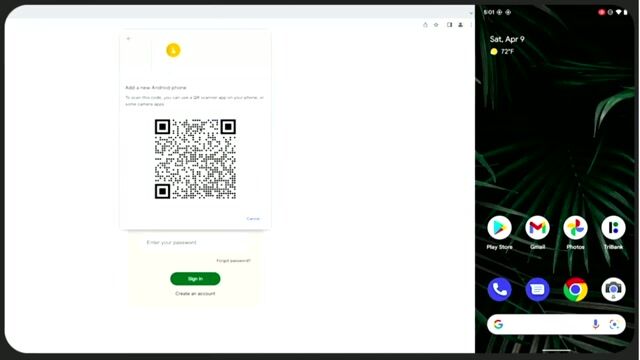
How passwordless authentication with magic links works
Passwordless authentication replaces traditional passwords with methods like magic links or one-time codes sent via email for a more secure login experience.
#4about 5 minutes
Securing accounts with multi-factor authentication layers
Multi-factor authentication adds a crucial security layer by requiring a second verification factor, such as an OTP, SMS code, or a physical security key.
#5about 2 minutes
Understanding the next generation of authentication with passkeys
Passkeys offer a phishing-resistant alternative to passwords by using device-based biometrics like fingerprints or face ID to create secure cryptographic keys.
#6about 5 minutes
How single sign-on simplifies access across applications
Single sign-on (SSO) uses a central identity provider to authenticate a user once, granting them access to multiple applications without separate logins.
#7about 2 minutes
A practical guide to adopting modern authentication methods
Successfully transitioning to modern authentication requires conducting a security assessment, choosing the right methods for your use case, and educating users.
#8about 2 minutes
Addressing SSO risks and account recovery options
The Q&A covers the security of a central SSO provider and the recovery mechanisms available when a user loses access to their phone for SMS-based authentication.
Related jobs
Jobs that call for the skills explored in this talk.
Matching moments
02:58 MIN
Understanding passwordless authentication technologies
Accelerating Authentication Architecture: Taking Passwordless to the Next Level

01:02 MIN
The future outlook for passkey authentication
Passwordless Web 1.5

03:04 MIN
Introducing passkeys for secure passwordless authentication
Passwordless Web 1.5
11:03 MIN
Q&A on career path and the future of passwordless
Accelerating Authentication Architecture: Taking Passwordless to the Next Level
03:23 MIN
The impact of Passkeys on passwordless adoption
Passwordless future: WebAuthn and Passkeys in practice
01:25 MIN
Shifting to modern possession and biometric factors
Passwordless future: WebAuthn and Passkeys in practice
03:01 MIN
Exploring the user experience flaws in web authentication
SSO with Ethereum and Next JS
03:02 MIN
The fundamental problems with password-based authentication
Passwordless future: WebAuthn and Passkeys in practice
Featured Partners
Related Videos
 32:32
32:32Passwordless future: WebAuthn and Passkeys in practice
Clemens Hübner
 30:21
30:21Passwordless Web 1.5
Paweł Łukaszuk
 16:05
16:05No More Post-its: Boost your login security with APIs
Alvaro Navarro
 49:52
49:52Accelerating Authentication Architecture: Taking Passwordless to the Next Level
Yedidya Schwartz
 44:49
44:49SSO with Ethereum and Next JS
Rahat Chowdhury
 23:42
23:42Delegating the chores of authenticating users to Keycloak
Alexander Schwartz
 31:19
31:19Skynet wants your Passwords! The Role of AI in Automating Social Engineering
Wolfgang Ettlinger & Alexander Hurbean
 29:31
29:31Break the Chain: Decentralized solutions for today’s Web2.0 privacy problems
Adam Larter
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.








