Tom Tovar
Thinking Differently - How to Make Money from Cyber Attacks & Cheats
#1about 3 minutes
Rethinking cyber attacks as a revenue opportunity
Instead of blocking all attacks, consider the user's intent and transform security events into monetization moments.
#2about 4 minutes
Understanding the scale and speed of mobile app attacks
Mobile apps are attacked within milliseconds of being published, with a significant percentage of the user base under attack at any given time.
#3about 2 minutes
Monetizing users on gray market gaming platforms
Instead of blocking users on emulators like BlueStacks, partner with the platform to charge a bounty for each player you allow.
#4about 3 minutes
Turning memory editing cheats into paid upgrades
When a player uses a tool like Game Guardian to edit memory for in-game currency, offer them the option to purchase those points legitimately.
#5about 2 minutes
Converting advanced cheaters into subscribers
For users employing advanced tools like Lucky Patcher, offer a subscription model that legitimizes their enhanced gameplay as a premium feature.
#6about 3 minutes
Creating a pro league for automated bot users
Channel users who run automated bots into a separate 'pro league' where they can compete against other bots, creating a new competitive tier.
#7about 2 minutes
Knowing which attacks should not be monetized
Distinguish between users trying to enhance their experience and malicious actors committing fraud or identity theft, which must always be blocked.
#8about 3 minutes
Implementing a framework for attack monetization
A successful monetization strategy requires a framework to detect attacks, provide telemetry data, and give developers control over the business logic outcome.
#9about 3 minutes
Q&A on common attacks and detection methods
The most common mobile gaming attack is memory editing, and reliable defense involves detecting the patching methods used by attackers on both the app and the defense itself.
Related jobs
Jobs that call for the skills explored in this talk.
Matching moments

02:39 MIN
Applying gaming anti-cheat lessons to cybersecurity
Outsmarting the System: What Game Cheaters Can Teach Us About Cyber Security
03:11 MIN
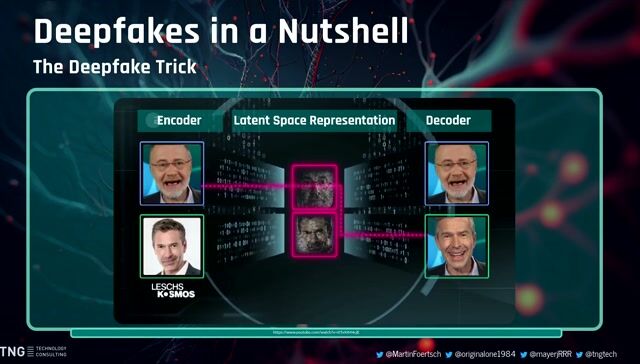
Demonstrating deepfake attacks and social engineering
The AI Elections: How Technology Could Shape Public Sentiment

02:26 MIN
Why developers make basic cybersecurity mistakes
Don't Be A Naive Developer: How To Avoid Basic Cybersecurity Mistakes

05:31 MIN
From vulnerability researcher to automated security founder
The transformative impact of GenAI for software development and its implications for cybersecurity

01:13 MIN
How Android and iOS successfully hardened their platforms
Simple Steps to Kill DevSec without Giving Up on Security

07:18 MIN
An overview of common social engineering attack techniques
Getting under the skin: The Social Engineering techniques
04:40 MIN
How attackers use AI to refactor exploits
The AI Security Survival Guide: Practical Advice for Stressed-Out Developers

03:26 MIN
How to protect yourself and your company from deepfakes
Deep Fakes: The Lies We Can’t See
Featured Partners
Related Videos
 17:31
17:31Outsmarting the System: What Game Cheaters Can Teach Us About Cyber Security
John Romero
 43:56
43:56Getting under the skin: The Social Engineering techniques
Mauro Verderosa
 27:32
27:32Security Pitfalls for Software Engineers
Jasmin Azemović
 2:08:06
2:08:06The attacker's footprint
Antonio de Mello & Amine Abed
 31:19
31:19Skynet wants your Passwords! The Role of AI in Automating Social Engineering
Wolfgang Ettlinger & Alexander Hurbean
 24:09
24:09Plants vs. Thieves: Automated Tests in the World of Web Security
Ramona Schwering
 57:47
57:47Cracking the Code: Decoding Anti-Bot Systems!
Fabien Vauchelles
 1:58:59
1:58:59Stranger Danger: Your Java Attack Surface Just Got Bigger
Vandana Verma Sehgal
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.




GULP Information Services GmbH
Remote
Flutter
Routing
Continuous Integration

Forensik.IT GmbH



Excellence AG
Kotlin
Kubernetes
Apache Kafka
Microservices
Continuous Delivery
+1
