Philipp Krenn
OPA for the cloud natives
#1about 3 minutes
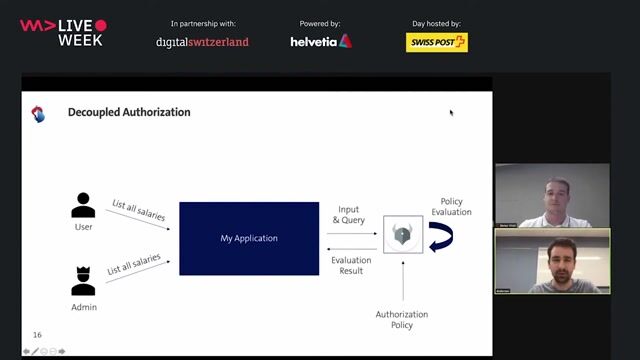
Decoupling security checks from application deployment
Traditional embedded security checks are hard to audit and maintain, so decoupling them as policy-as-code enables continuous validation and simplifies compliance.
#2about 3 minutes
Shifting security left to prevent incidents before deployment
Proactively catching security violations in the CI pipeline is far better than reacting to incidents in production, moving beyond tribal knowledge to codified policies.
#3about 3 minutes
Introducing the Open Policy Agent (OPA) and Rego
OPA is a CNCF graduated project that provides a unified way to enforce policies across APIs using a custom declarative language called Rego.
#4about 3 minutes
Writing basic Rego policies for common use cases
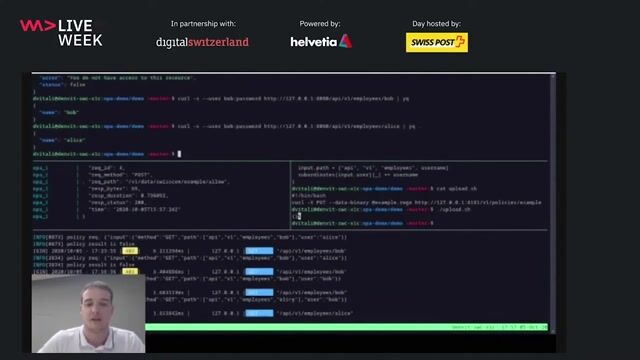
Simple Rego policies can enforce rules like user data access control, manager hierarchies, or ensuring Kubernetes pods use a trusted container registry.
#5about 5 minutes
Using the OPA Playground to test and debug policies
The OPA Playground provides an interactive environment for writing, testing, and debugging Rego policies against sample input data, such as Kubernetes configurations.
#6about 2 minutes
Exploring OPA deployment patterns and advanced use cases
OPA can be deployed as a Go library or a sidecar daemon, enabling advanced use cases like validating Elasticsearch queries to enforce fine-grained data access control.
#7about 3 minutes
Automating infrastructure compliance with CIS benchmarks
OPA policies can codify Center for Internet Security (CIS) benchmarks to continuously scan Kubernetes clusters for misconfigurations and security vulnerabilities.
#8about 3 minutes
Addressing performance and adoption challenges with OPA
While powerful, OPA adoption can be hindered by the complexity of writing performant queries and the learning curve associated with its custom language, Rego.
#9about 3 minutes
Answering audience questions about OPA and Rego
The Q&A covers Rego's support for JSON and YAML, deployment options on bare metal or VMs, and potential integrations with APIs like GraphQL.
Related jobs
Jobs that call for the skills explored in this talk.
Matching moments
04:00 MIN
Introducing Open Policy Agent for custom policies
A practical guide to writing secure Dockerfiles

03:11 MIN
Exploring other use cases for OPA beyond web APIs
Decoupled Authorization using Policy as Code
22:06 MIN
Q&A on policy culture, tooling, and security
Policy as [versioned] code - you're doing it wrong
06:29 MIN
Introducing Policy as Code and Open Policy Agent
Decoupled Authorization using Policy as Code

01:21 MIN
Automating policy enforcement with admission controllers
Kubernetes Security Best Practices
03:27 MIN
How OPA works with a simple Rego policy
Decoupled Authorization using Policy as Code

02:23 MIN
Demo of basic policy evaluation using OPA
Decoupled Authorization using Policy as Code
04:25 MIN
Dynamically updating authorization policies without downtime
Decoupled Authorization using Policy as Code
Featured Partners
Related Videos
 32:16
32:16Decoupled Authorization using Policy as Code
Anderson Dadario & Denys Vitali
![Policy as [versioned] code - you're doing it wrong](https://customer-goifxnzhrq3d0d54.cloudflarestream.com/23fa4a514c18f0a9b39573f31d96ba54/thumbnails/thumbnail.jpg?time=33000ms) 45:57
45:57Policy as [versioned] code - you're doing it wrong
Chris Nesbitt-Smith
 23:29
23:29Delay the AI Overlords: How OAuth and OpenFGA Can Keep Your AI Agents from Going Rogue
Deepu
 1:00:00
1:00:00Un-complicate authorization maintenance
Alex Olivier
 30:07
30:07External Secrets Operator: the secrets management toolbox for self-sufficient teams
Moritz Johner
 23:26
23:26Great DevEx and Regulatory Compliance - Possible?
Martin Reynolds
 23:08
23:08Kubernetes Security Best Practices
Rico Komenda
 33:20
33:20DevSecOps: Security in DevOps
Aarno Aukia
Related Articles
View all articles


.gif?w=240&auto=compress,format)
From learning to earning
Jobs that call for the skills explored in this talk.


iits-consulting GmbH
Munich, Germany
Intermediate
Go
Docker
DevOps
Kubernetes

SYSKRON GmbH
Regensburg, Germany
Intermediate
Senior
.NET
Python
Kubernetes

smartclip Europe GmbH
Hamburg, Germany
Intermediate
Senior
GIT
Linux
Python
Kubernetes

adconova GmbH
Docker
Terraform
Kubernetes
Elasticsearch
Microsoft Office
+2

Codasip
Berlin, Germany



Codasip
Dresden, Germany