Adrian Mouat
Supply Chain Security and the Real World: Lessons From Incidents
#1about 6 minutes
Moving beyond abstract security metaphors and vague advice
Security advice often relies on unhelpful abstractions, but real-world incidents provide concrete, actionable guidance for developers.
#2about 3 minutes
Analyzing the Codecov breach and its attack vector
The Codecov breach occurred when a secret in a Docker image led to a modified script that exfiltrated CI/CD environment variables.
#3about 5 minutes
Securing Docker builds and verifying script downloads
Prevent secret leaks in Dockerfiles by using the `--secret` flag and always verify downloaded scripts with checksums or GPG signatures.
#4about 2 minutes
The risks of storing secrets in environment variables
Storing secrets in environment variables makes them easy to exfiltrate, so prefer identity federation, secret managers, or temporary files instead.
#5about 5 minutes
Deconstructing the `changed-files` GitHub Action attack
A compromised dependency (`reviewdog`) was used to inject malicious code into the `changed-files` action, targeting Coinbase in a multi-stage attack.
#6about 2 minutes
Hardening GitHub repositories and pinning dependencies
Mitigate attacks by enforcing commit signing, restricting tag updates, and pinning GitHub Actions to a specific content digest.
#7about 2 minutes
Replacing long-lived credentials with short-lived tokens
Eliminate a common attack vector by replacing long-lived credentials with short-lived tokens generated via identity federation like OIDC.
#8about 1 minute
Summary of actionable supply chain security advice
A final recap covers key actions like verifying downloads, avoiding secrets in environment variables, pinning actions, and using short-lived credentials.
Related jobs
Jobs that call for the skills explored in this talk.
Matching moments
04:45 MIN
Mitigating supply chain attacks with DevSecOps practices
Security Pitfalls for Software Engineers

01:46 MIN
Understanding the rising threat to software supply chains
Open Source Secure Software Supply Chain in action
02:33 MIN
Key takeaways and next steps for securing your supply chain
Securing your application software supply-chain

01:52 MIN
Securing container images and the software supply chain
Security Challenges of Breaking A Monolith
01:31 MIN
Exploring the core domains of supply chain security
Open Source Secure Software Supply Chain in action
01:25 MIN
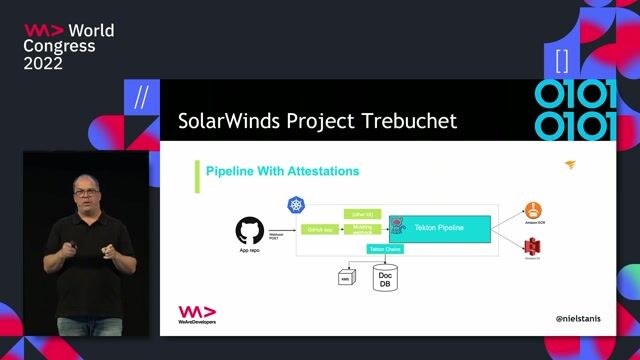
Learning from the SolarWinds supply chain attack
Securing your application software supply-chain
02:25 MIN
Implementing and enforcing supply chain policies
Securing your application software supply-chain
05:36 MIN
Taking action on NPM supply chain security vulnerabilities
WeAreDevelopers LIVE - Build a multi AI agents game master with Strands & our weekly web finds
Featured Partners
Related Videos
 28:27
28:27Securing your application software supply-chain
Niels Tanis
 29:50
29:50Real-World Security for Busy Developers
Kevin Lewis
 25:28
25:28How GitHub secures open source
Joseph Katsioloudes
 32:55
32:55Open Source Secure Software Supply Chain in action
Natale Vinto
 21:53
21:53Simple Steps to Kill DevSec without Giving Up on Security
Isaac Evans
 37:36
37:36Walking into the era of Supply Chain Risks
Vandana Verma
 27:32
27:32Security Pitfalls for Software Engineers
Jasmin Azemović
 46:36
46:36Hacking Kubernetes: Live Demo Marathon
Andrew Martin
Related Articles
View all articles.gif?w=240&auto=compress,format)

.png?w=240&auto=compress,format)

From learning to earning
Jobs that call for the skills explored in this talk.

Codasip
Berlin, Germany




Taktile GmbH
Berlin, Germany
Remote
Intermediate
DevOps
Gitlab
Terraform
Continuous Delivery
+1

Koda Staff


Computacenter AG & Co. OHG
Remote
Intermediate
GIT
Linux
Kubernetes
Continuous Integration

NTT DATA Deutschland GmbH
Remote
Node.js
Continuous Integration