Niels Tanis
Reviewing 3rd party library security easily using OpenSSF Scorecard
#1about 4 minutes
Understanding the inherent risks of third-party dependencies
The vast majority of an application's code comes from third-party libraries, creating significant risk as shown by the Log4j vulnerability.
#2about 2 minutes
How malicious actors infiltrate open source projects
Malicious actors can introduce backdoors into trusted projects over long periods, as demonstrated by the XZ Utils supply chain attack.
#3about 2 minutes
Detecting known vulnerabilities and hidden package dependencies
Tooling can help identify publicly disclosed vulnerabilities, but risks remain from unmanaged or hidden dependencies bundled within packages.
#4about 2 minutes
Introducing OpenSSF Scorecard as a software nutrition label
OpenSSF Scorecard provides a "nutrition label" for open source projects by running automated checks to assess their security posture.
#5about 3 minutes
Breaking down key security checks in Scorecard
Scorecard evaluates projects based on the presence of known vulnerabilities, automated dependency updates, security policies, and the use of testing like fuzzing and SAST.
#6about 3 minutes
Evaluating project health and build process integrity
Scorecard assesses repository health through checks for branch protection, code reviews, contributor diversity, pinned dependencies, and signed releases.
#7about 2 minutes
Applying Scorecard to analyze a real-world package
A practical demonstration shows how to run Scorecard against a popular library like Newtonsoft.Json and use its API to analyze transitive dependencies.
#8about 3 minutes
Correlating Scorecard results with real-world security data
Research shows a strong correlation between higher OpenSSF Scorecard scores and better security outcomes, such as fewer vulnerabilities and more active maintenance.
#9about 3 minutes
Exploring the future of automated security analysis
Future improvements in security tooling should focus on deeper analysis like coverage-based fuzzing, data-flow SAST, build reproducibility, and community-based auditing.
#10about 1 minute
Final takeaways on integrating Scorecard into your workflow
Scorecard is a valuable tool for assessing project health but should be used as part of a broader security strategy, not as an end goal.
Related jobs
Jobs that call for the skills explored in this talk.
Matching moments
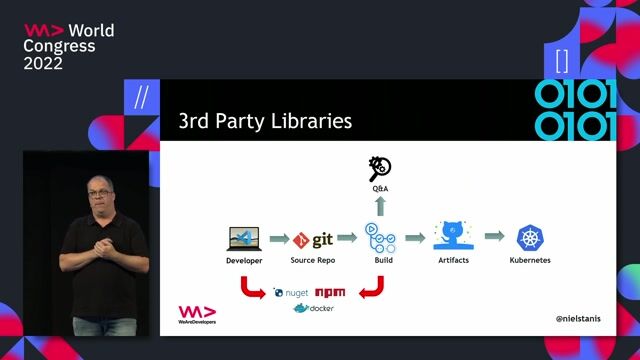
04:46 MIN
Managing risks from third-party libraries
Securing your application software supply-chain

05:19 MIN
Managing third-party software dependencies for security
Software Security 101: Secure Coding Basics
02:50 MIN
Managing security risks in third-party dependencies
A Primer in Single Page Application Security (Angular, React, Vue.js)
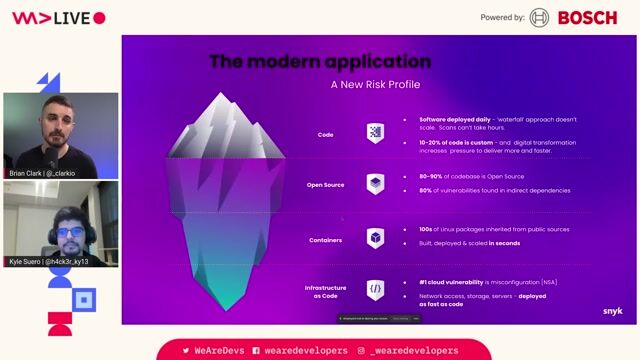
06:14 MIN
The risks of open source and indirect dependencies
Maturity assessment for technicians or how I learned to love OWASP SAMM
02:56 MIN
Q&A on vulnerable libraries and team security responsibility
Security Pitfalls for Software Engineers

04:14 MIN
The scale and challenge of securing open source
How GitHub secures open source
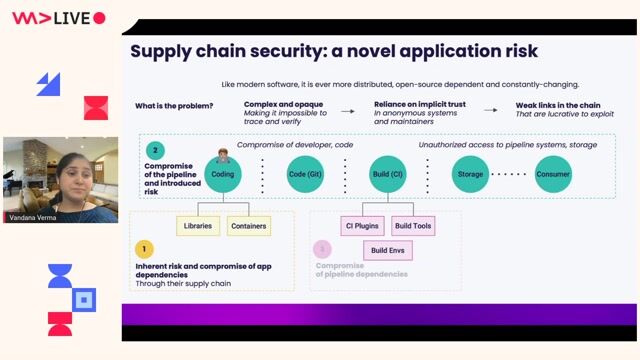
03:50 MIN
Building a foundation for pipeline security
Walking into the era of Supply Chain Risks
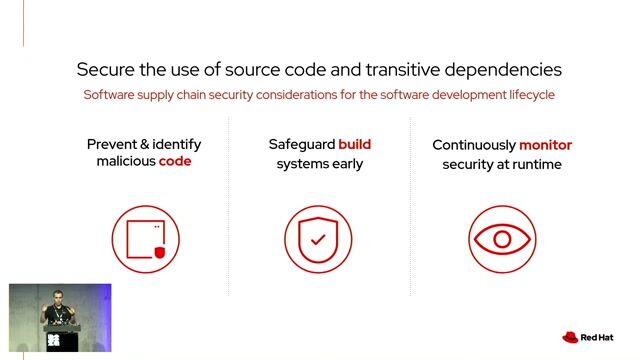
04:51 MIN
Using open source tools to secure the entire SDLC
Open Source Secure Software Supply Chain in action
Featured Partners
Related Videos
 28:27
28:27Securing your application software supply-chain
Niels Tanis
 32:55
32:55Open Source Secure Software Supply Chain in action
Natale Vinto
 25:28
25:28How GitHub secures open source
Joseph Katsioloudes
 29:50
29:50Real-World Security for Busy Developers
Kevin Lewis
 21:53
21:53Simple Steps to Kill DevSec without Giving Up on Security
Isaac Evans
 26:59
26:59Security in modern Web Applications - OWASP to the rescue!
Jakub Andrzejewski
 23:34
23:34Secure Code Superstars: Empowering Developers and Surpassing Security Challenges Together
Stefania Chaplin
 08:27
08:27Get security done: streamlining application security with Aikido
Mia Neethling
Related Articles
View all articles
.png?w=240&auto=compress,format)


From learning to earning
Jobs that call for the skills explored in this talk.

Codasip
Berlin, Germany

Workwise GmbH

NTT DATA Deutschland GmbH
Remote
Node.js
Continuous Integration

NTT DATA Deutschland GmbH
Remote
Node.js
Continuous Integration

NTT DATA Deutschland GmbH
Remote
Node.js
Continuous Integration

Codasip
Dresden, Germany

Fraunhofer-Gesellschaft

